High-profile data thefts from companies such as Yahoo 1 and Uber 2 are making the general public more aware of the dangers posed by cyber criminals. But the attentions of these individuals are not just focused on the financial benefits of stealing private information or using ransom ware to blackmail victims. There are a number who prefer the chaos caused by sabotaging public events, whether for monetary gain, notoriety or simply for fun.
Due to the amount of people taking part, the attention garnered by such attacks can be immense. And for those whose cyber crimes are more organised and with purpose, social events are perfect vectors to get their message heard – especially if the event is heavily publicised.
Tactics have varied between events, but most appear to be attempts to interrupt the festivities, usually through infrastructure disruptions. Other more nefarious tactics include the use of malware to spy on attendees.
Affected Events
2018 Winter Olympics
The most recent example of events being targeted was the 2018 Winter Olympics where a cyber attack caused a number of technological problems 3. Concerns were raised after WiFi provision in both the venue and the press centre ceased shortly before the opening ceremony, and problems with the Pyeongchang 2018 website forced it to be taken down. The website issues meant that users were unable to print pre-purchased tickets for the events.
Although the issues at the Winter Olympics didn’t disrupt any of the events, nor compromise the safety and security of athletes or spectators, the issue could have been much worse had no information security precautions been taken.
CyCon 2017
Attendees of a cyber security conference – CyCon 2017 – were being targeted with a fake flyer containing Malware 4. The flyer aesthetics were based on information taken from the convention’s own website, meaning that the flyers appeared to be legitimate at first glance.
2012 Olympic Games
The 2012 Olympic Games in London also raised concerns 5. Though the main threat did not materialise, there were fears about Britain’s electricity infrastructure being unable to cope with a cyber-attack, resulting in lighting failures at the Olympic venues.
2003 Pan American Games
In 2003, the Pan American Games were affected by malware 6. The virus compromised internal systems and prevented the media from accessing the latest scores and results from competitions.
Protecting events from Cyber Attacks
Terrorism, organised crime, public disorder and natural events are all possible problems encountered by large public event and it takes a great deal of preparation in order to manage and minimise the effects of such activities.
Here are some key security activities you should undertake when hosting a large public event:
Physical Security
Spend time making sure that the entire infrastructure behind the event, including all interrelated systems, has been reviewed and every possible vulnerability assessed.
An impact analysis – as recommended through ISO 22301 – can help with this. An impact analysis requires you to identifying each source of disruption, determine how this will affect your event, and establish how likely it is to occur. Through this, you will be able to pinpoint prevention techniques to mitigate the risk, and plan recovery activities should the worst occur.
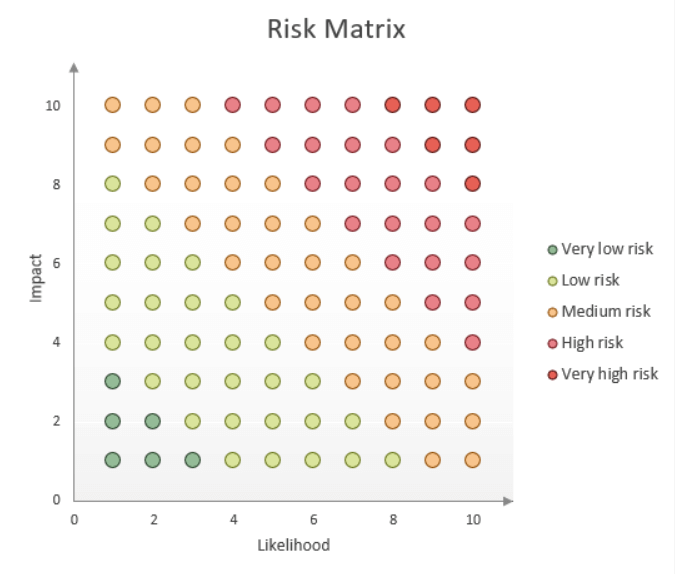
You can prioritise your prevention and recovery activities using a risk matrix. You will need to score the likeliness that the disruption will occur (1 = not likely, 10 = very likely) against the impact that the disruption would have, should it occur (1 = minimal impact, 10 = significant impact) to establish the overall risk score.
IT Security
In the case of the IT infrastructure, keeping up-to-date with the latest security vulnerabilities is particularly advisable. The landscape of cyber security is constantly changing and although the systems used by events may already have been determined before specific vulnerabilities emerge, being aware of the types of attack risks that could happen means that you will be better prepared to overcome them should they arise.
For example, a number of high-profile cyber attacks occurred around the same time as the 2012 Olympic Games and although the planners could not have taken into account those specific events before they happened, it was then prepared for attacks involving those techniques 7.
Particularly vulnerable IT systems are those that are accessible via the internet. These systems should have particular attention paid to them. On this topic, the chief information officer for the London 2012 Olympic Games, Gerry Pennell, advised:
“keep mission-critical games systems quite isolated from anything web-facing. So very much partitioned and separated, thus making it hard for an external attack to succeed”
Continuously testing your systems against known vulnerabilities can help identify areas or risk and provide insight, reassuring you that your systems are robust enough to withstand an attack.
ISO 27001 is an internationally recognised standard for best-practice information security management which means it can help businesses identify and manage the tools required to protect the IT infrastructure supporting their events against attack. It can also help to protect their information assets, and the information of their customers, from being accessed, corrupted, lost or stolen.
Find Out More
If you are interested in the benefits that ISO 22301 or ISO 27001 can bring to your business, please contact one of our experienced Certification Development Consultants on 0333 344 3646.
Footnotes:
1. Article from the BBC ↩
2. Article from the BBC ↩
3. Article from The Guardian ↩
5. Article from the BBC ↩
6. Article from The Register ↩
7. Article from the BBC ↩

